Managed Security Services
Keeping up with security threats and compliance mandates is an around-the-clock effort. Ntirety keeps your environment secure, so you can focus on your business.
Get StartedComprehensive Protection
A strong security posture today requires technical expertise, advanced tools, and a multi-faceted approach in an environment where skilled cybersecurity personnel are in short supply and bad actors are increasingly sophisticated.
Ntirety Managed Security Services offers a comprehensive, industry-aligned security solution for organizations seeking to maintain focus on their core business while meeting stringent security and compliance requirements.
Critical Security Challenges Organizations Face
Expanded Threat Perimeter
Distributed users and an explosion of access points add complexity
Drowning in Point Solutions
The patchwork of vendors can leave unseen security gaps
Increasing Demands Strain Bandwidth
As much as 80% of IT’s time is spent on repetitive operations
Budget and Skills Shortfall
Cybersecurity skills deficit and IT resource constraints put additional strain on IT
Security Solution Spectrum
How you solve your security needs can be complex. You must find a solution to meet each potential security vulnerability and decide how to manage it. There is a spectrum of solutions that ranges from self-managed to fully outsourced with hybrid models in between.
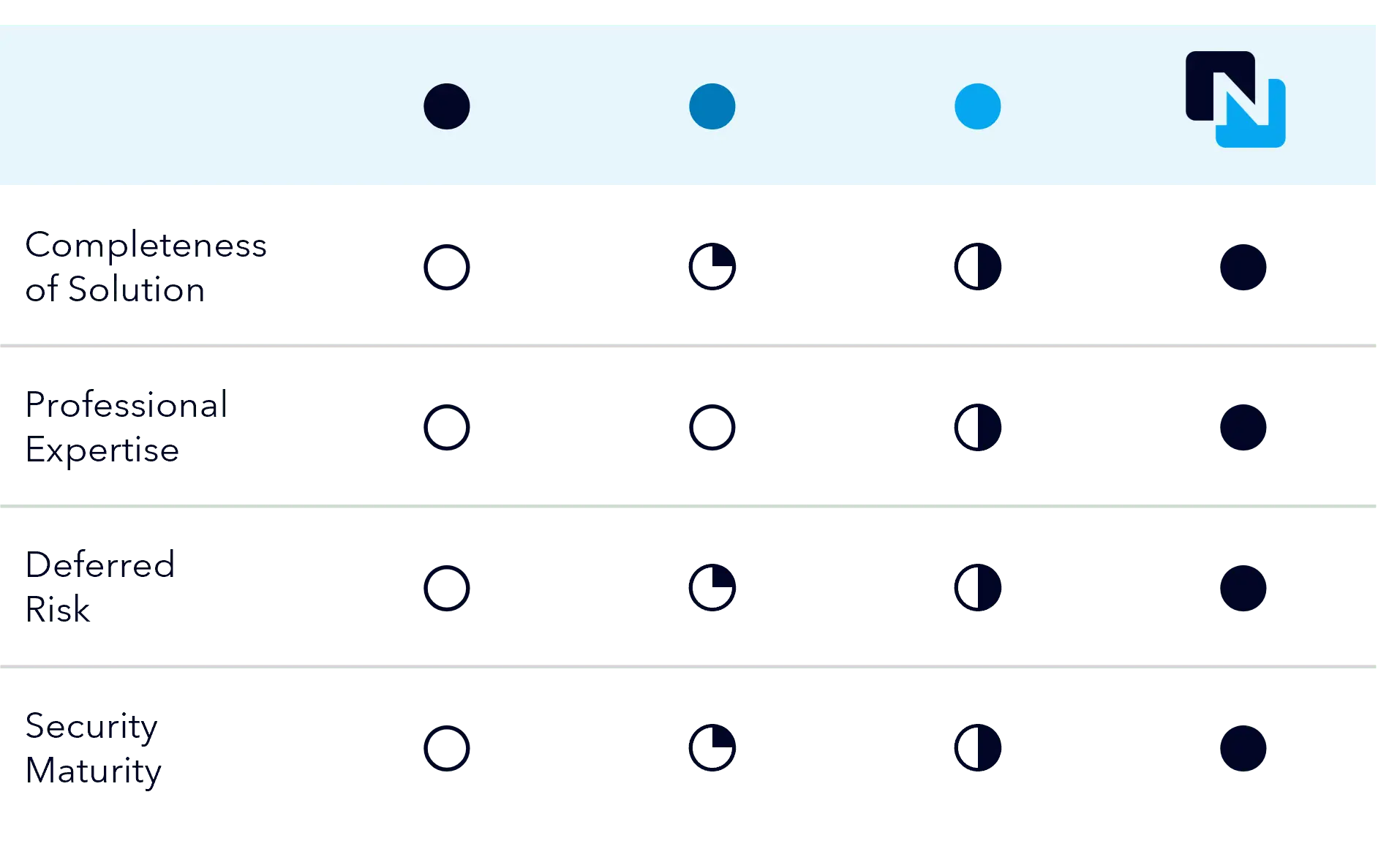
The Benefits of Ntirety’s Full-Stack Security Solution
Secure your entire IT stack with the best people, processes, and technology available today.
Unparalleled Professional Expertise
Seasoned security experts bring extensive experience
Best-in-Class
Technology
Cutting-edge security tools and platforms
Proactive Threat
Response
Decisive action to resolve security incidents
Comprehensive IT Support
End-to-end IT solutions across your stack
Compliance-Driven Approach
Aligned with industry compliance standards

A Framework for Comprehensive Security
Ntirety security solutions span all facets of the NIST Cybersecurity Framework so organizations can attain a mature, industry-standard security posture.
Select each stage to see available services
Protect
Implement safeguards
Detect
Uncover threats in your environment
The Ntirety Process for Ironclad Security
1
Assess
Learn Where You Are Today
2
Advise
Get a Roadmap to Where You Want to Go
3
Resolve
Execute Your Plan
4