What Is the NIST Cybersecurity Framework?
The NIST Cybersecurity Framework is a set of guidelines and best practices designed to help organizations manage and reduce cybersecurity risks. Developed by the National Institute of Standards and Technology (NIST), this framework is widely recognized and used by organizations across various industries to improve their cybersecurity defenses.
Key Benefits of the NIST Framework
- Comprehensive Coverage: The NIST framework covers all aspects of cybersecurity, from identifying potential risks to responding to and recovering from incidents. This comprehensive approach ensures that no part of your cybersecurity strategy is overlooked.
- Customizable to Your Needs: One of the strengths of the NIST framework is its flexibility. It can be tailored to fit the specific needs and resources of your organization, regardless of size or industry.
- Alignment with Business Goals: The framework helps align cybersecurity efforts with your organization’s business objectives. This ensures that your cybersecurity strategy supports and enhances your business goals rather than hindering them.
- Improved Risk Management: By following the NIST framework, organizations can better identify, assess, and manage cybersecurity risks. This proactive approach helps in prioritizing and addressing the most critical threats.
- Enhanced Incident Response: The NIST framework includes guidelines for responding to and recovering from cybersecurity incidents. This ensures your organization is prepared to handle incidents effectively, minimizing damage and reducing recovery time.
- Compliance and Best Practices: Implementing the NIST framework can help organizations comply with regulatory requirements and industry standards. It also ensures that you are following cybersecurity best practices recognized globally.
How the NIST Framework Works
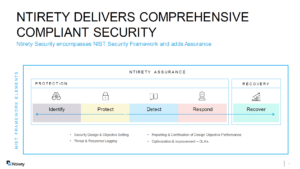
The NIST Cybersecurity Framework is organized into five core functions:
- Identify: Develop an understanding of your environment to manage cybersecurity risk to systems, assets, data, and capabilities.
- Protect: Implement appropriate safeguards to ensure the delivery of critical services.
- Detect: Develop and implement activities to identify the occurrence of a cybersecurity event.
- Respond: Be prepared to act regarding a detected cybersecurity event.
- Recover: Maintain plans for resilience and restore any capabilities or services impaired due to a cybersecurity event.
These functions provide a high-level, strategic view of the lifecycle of an organization’s management of cybersecurity risk.
Why Adopt the NIST Framework?
Adopting the NIST Cybersecurity Framework is a strategic move that can significantly strengthen your organization’s cybersecurity posture. It provides a structured approach to managing cybersecurity risks and ensures that your efforts are comprehensive, effective, and aligned with your business goals. By implementing the NIST framework, you can enhance your organization’s resilience against cyber threats and ensure that you are well-prepared to handle incidents that may arise.
How to Align Your Organization with the NIST Framework
Ntirety has developed a self-service, online security assessment to help organizations identify and address cybersecurity gaps and risks. The free assessment consists of 10 questions aligned with the NIST framework, covering the key areas: Identify, Protect, Detect, Respond, Recover. Upon completion, you’ll receive a comprehensive report with tailored recommendations for each area, prioritized to help you tackle the most critical gaps first. This report is an excellent first step in upgrading your organization’s cybersecurity posture.
Click here to take the assessment and get started.
Ntirety is the leader in comprehensive managed services, partnering with organizations to modernize and secure today’s complex IT environment. Ntirety’s solutions span cloud infrastructure, cybersecurity, data, and compliance, connecting mission-critical data across highly secure, available, and resilient environments.
If you’re looking to take the next steps in understanding and implementing the NIST CSF for your organization, the experts at Ntirety can help. Request a consultation to get started.